Overview
Generate TOTP codes for testing two-factor authentication flows. The step creates valid 6-digit codes that refresh every 30 seconds, automatically waits if a code is about to expire, and stores the result in a variable for use in subsequent steps like Fill.Setting Up Your Secret Token
Before adding this step, obtain your TOTP secret from the application you’re testing.If the application shows a text token
- Navigate to your app’s 2FA or security settings
- Look for “Manual Entry” or “Can’t scan QR code?”
- Copy the secret token (usually looks like
JBSWY3DPEHPK3PXP) - Store it as an environment variable in Supatest
If only a QR code is shown
- Screenshot the QR code during 2FA setup
- Use Token2 QR Decoder to extract the secret
- Copy the extracted token
- Store it as an environment variable in Supatest
Store the token securely
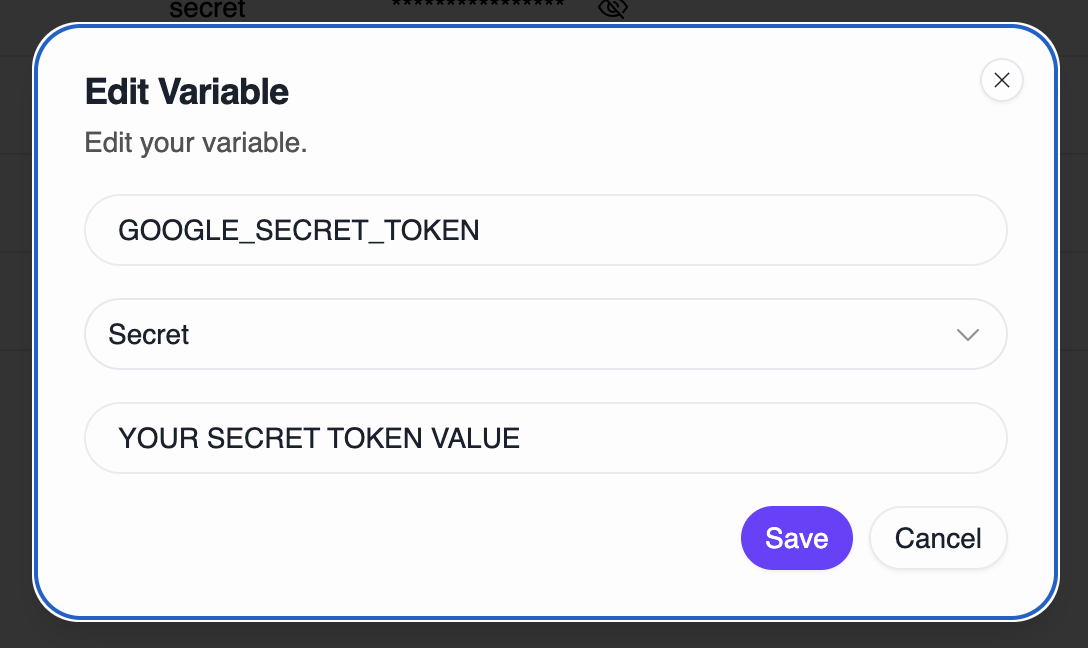
Recommended approach:- Go to your Supatest environment settings
- Create a new variable (e.g.,
TOTP_SECRET) - Set the type to secret so the value is masked
- Paste your token as the value
- Reference it in the step as
{{env.TOTP_SECRET}}
Using the Step
Add the Get TOTP Code step after actions that trigger 2FA (like clicking “Log In”). The form has two fields:- Secret Token: Enter
{{env.TOTP_SECRET}}or paste a token directly (not recommended for security) - Variable: Auto-generated name like
supatest_totp_0that stores the 6-digit code
Token format flexibility
The step accepts various formats and automatically cleans them:- Plain:
JBSWY3DPEHPK3PXP - Spaces:
JBSW Y3DP EHPK 3PXP - Dashes:
JBSW-Y3DP-EHPK-3PXP - Lowercase:
jbswy3dpehpk3pxp
Response Format
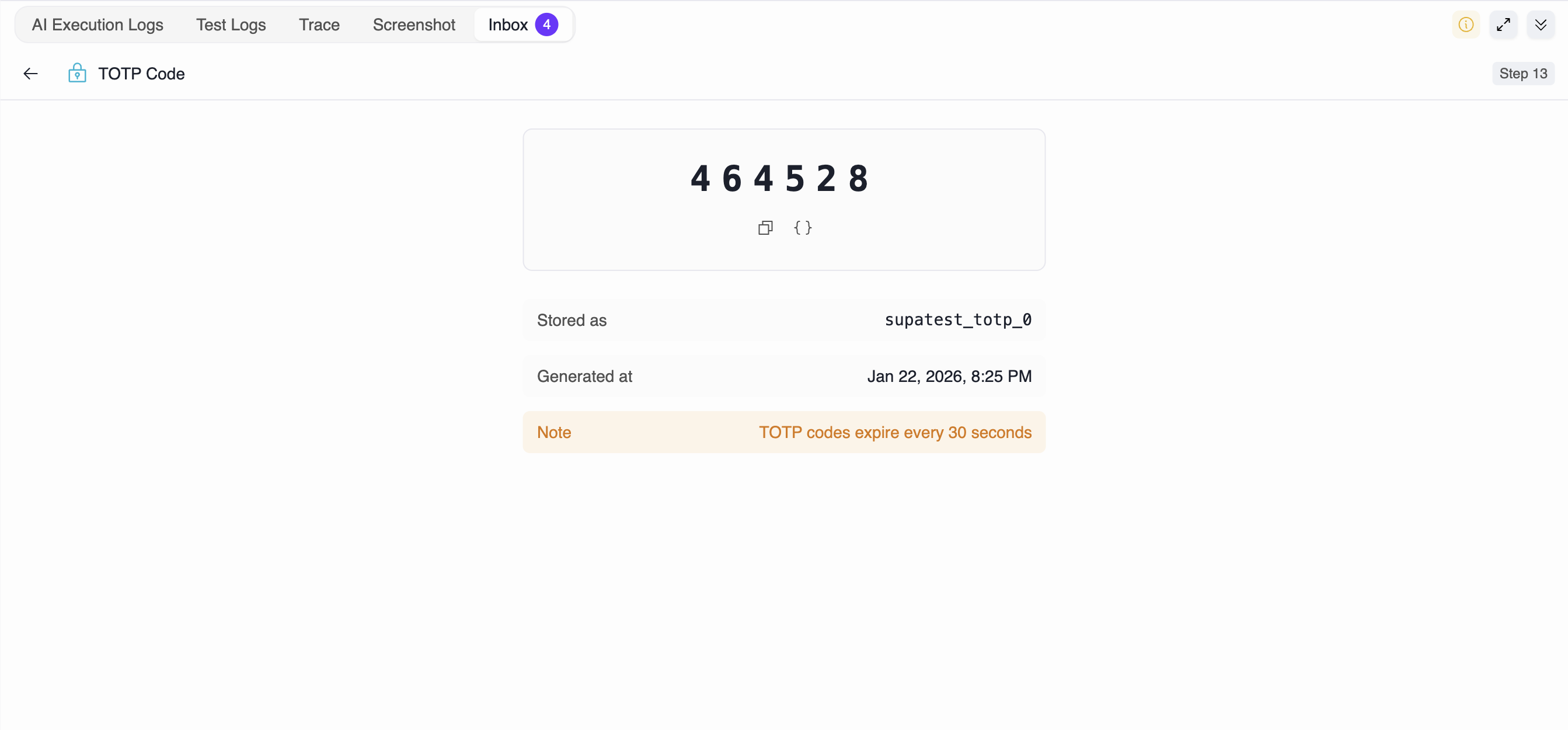
When the Get TOTP Code step executes, it generates a 6-digit numeric code and stores it as a string in the specified variable.Generated Value
Variable name:supatest_totp_0 (auto-generated)
Stored value: "123456" (example - actual code changes every 30 seconds)
Accessing the TOTP Code
In Fill steps:- Enable “Use variables” toggle
- Select the TOTP variable:
${supatest_totp_0} - The 6-digit code will be entered into the field
- Reference as:
{{vars.supatest_totp_0}} - Or:
{{vars['supatest_totp_0']}}
- Include in body:
{"code": "{{vars.supatest_totp_0}}"} - Include in headers:
Authorization: TOTP {{vars.supatest_totp_0}}
Using the Editor Console Inbox (Recommended)
The easiest way to get the TOTP code expression is to use the Inbox in the Editor Console. This eliminates the need to manually type variable names. Workflow:- Run your test until the Get TOTP Code step - Use “Run From Step” or run the test partially until the Get TOTP Code step completes
- Open the Inbox tab in the Editor Console (bottom panel)
- Click on the TOTP entry to view its details
- Copy the expression using the curly braces icon
{...}next to the code - Paste the expression directly into your next step (Fill, API Request, etc.)
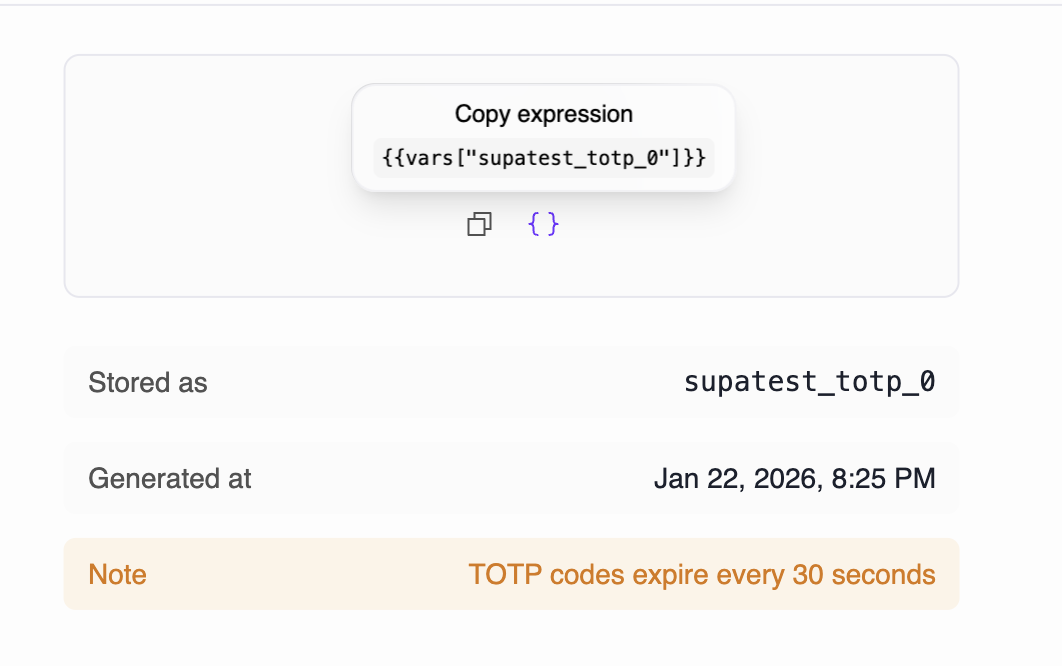
- Copy icon - Copies the actual code value (e.g.,
123456) - Curly braces icon
{...}- Copies the expression (e.g.,{{vars["supatest_totp_0"]}})
Example Values
The step generates standard 6-digit TOTP codes like:"042891""738291""000123""999887"
Multiple TOTP Steps
If you use multiple Get TOTP Code steps in a test (e.g., for different accounts), each creates a unique variable:- First step:
supatest_totp_0→"123456" - Second step:
supatest_totp_1→"789012" - Third step:
supatest_totp_2→"345678"
Example: Login with 2FA
Goal: Automate a complete login flow including two-factor authentication. Steps 1-3: Set up the login flow- Fill → Email field with
test@example.com - Fill → Password field with
{{env.TEST_PASSWORD}} - Click → Login button
{{env.TOTP_SECRET}}
Step 5: Get the expression from the Inbox
- Run the test until Step 4 completes
- Open the Inbox tab in the Editor Console
- Click on the TOTP entry
- Click the curly braces icon
{...}to copy the expression - Add a Fill step for the 2FA code field and paste the expression
Best Practices
Security:- Always store tokens in environment variables marked as secrets
- Use separate test accounts for automation, not real user accounts
- Rotate tokens periodically and store backup codes separately
- Let the step handle timing; don’t add manual waits
- Verify time synchronization if codes are consistently rejected
- Use descriptive variable names for multiple accounts (e.g.,
ADMIN_TOTP_SECRET,USER_TOTP_SECRET)
- Each step creates a unique variable:
supatest_totp_0,supatest_totp_1, etc. - Reference them in Fill steps via
{{vars.supatest_totp_0}} - Codes remain valid for at least 15 seconds after generation
Troubleshooting
”Secret token is empty after sanitization”
The token contains invalid characters. TOTP secrets must be base32 (A-Z and 2-7). Fix:- Check the environment variable is set correctly
- Verify no typos in
{{env.TOTP_SECRET}} - Re-extract the token from the QR code if copied incorrectly
Code not accepted by the application
Common causes:- Time mismatch: Test runner clock differs from server time
- Wrong secret: Token doesn’t match the one configured in the app
- Expired code: Long delays between generation and submission (check for slow steps or waits)
- Verify system time is accurate on your test runner
- Re-setup 2FA in the application to get a fresh token
- Check if the app uses a non-standard interval (some use 60 seconds instead of 30)
Environment variable not resolving
The step shows{{env.TOTP_SECRET}} literally instead of the value.
Fix:
- Ensure the variable exists in the environment selected for the test run
- Variable names are case-sensitive, confirm exact match
- Check the variable has a value assigned (not blank)
Multiple accounts generate the same code
Each account must have its own secret token. The step only generates different codes if given different secrets. Fix:- Create separate environment variables:
ADMIN_TOTP_SECRET,USER_TOTP_SECRET - Use the correct variable for each account’s Get TOTP Code step
- Verify each step stores to a different variable:
supatest_totp_0,supatest_totp_1
Related Steps
- Fill: Enter the generated code into 2FA input fields
- Navigate: Navigate to 2FA setup pages
- Run Python: Complex token handling or custom TOTP logic
- API Request: Fetch TOTP secrets dynamically from APIs
- Check Email: Alternative verification via email codes

